Software Defined Networks Penetration Testing
Intelligence Driven Cyber Security Operations
Software Defined Networks Penetration Testing
A Software-Defined Network (SDN) is a network framework characterized by a centralized, highly programmable controller that possesses a comprehensive view of a network’s paths and devices, effectively functioning as a singular configuration hub.
SDN penetration testing involves assessing the security of Software-Defined Networks. It includes preparing objectives, understanding SDN components, identifying risks, assessing vulnerabilities, exploiting weaknesses, analyzing the impact, reporting findings, addressing issues, validating fixes, and documenting the entire process. The goal is to ensure the security of SDN systems and protect against potential threats.
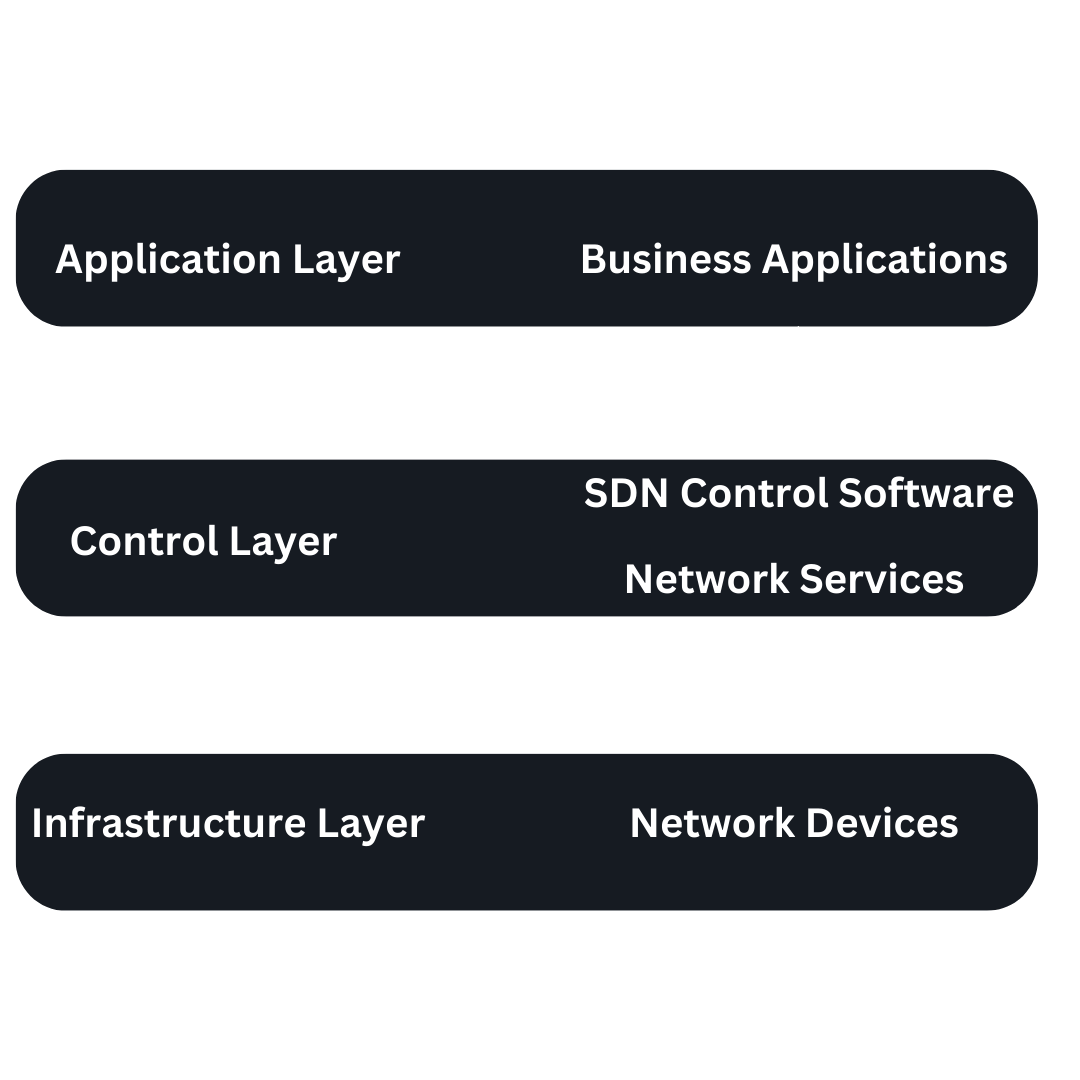
This paradigm shift towards automation provides significant benefits to enterprise networks. The diagram portrays the distinct layers within the SDN architecture and showcases their interactions:
Traditionally, in the conventional networking stack, each component handles both control and data functions. However, in SDNs, these two aspects are decoupled. The subsequent illustration highlights the contrast between the…
Software-Defined Network Penetration Testing
Our approach to Software-Defined Networking Pentesting


























